SSO
The Akuity Platform allows you to configure a single SSO provider for Kargo, such as Dex, OIDC, or any other supported providers, ensuring secure user access to your Kargo instance.
The Akuity Platform supports the following SSO providers:
- Dex
- OpenID Connect (OIDC)
For more detailed information on Kargo SSO, please refer to the documentation of OSS Kargo.
Below are the steps to configure SSO for Kargo using Dex and Okta as an example.
Configuring SSO
-
In your Kargo Instance, go to Settings.
-
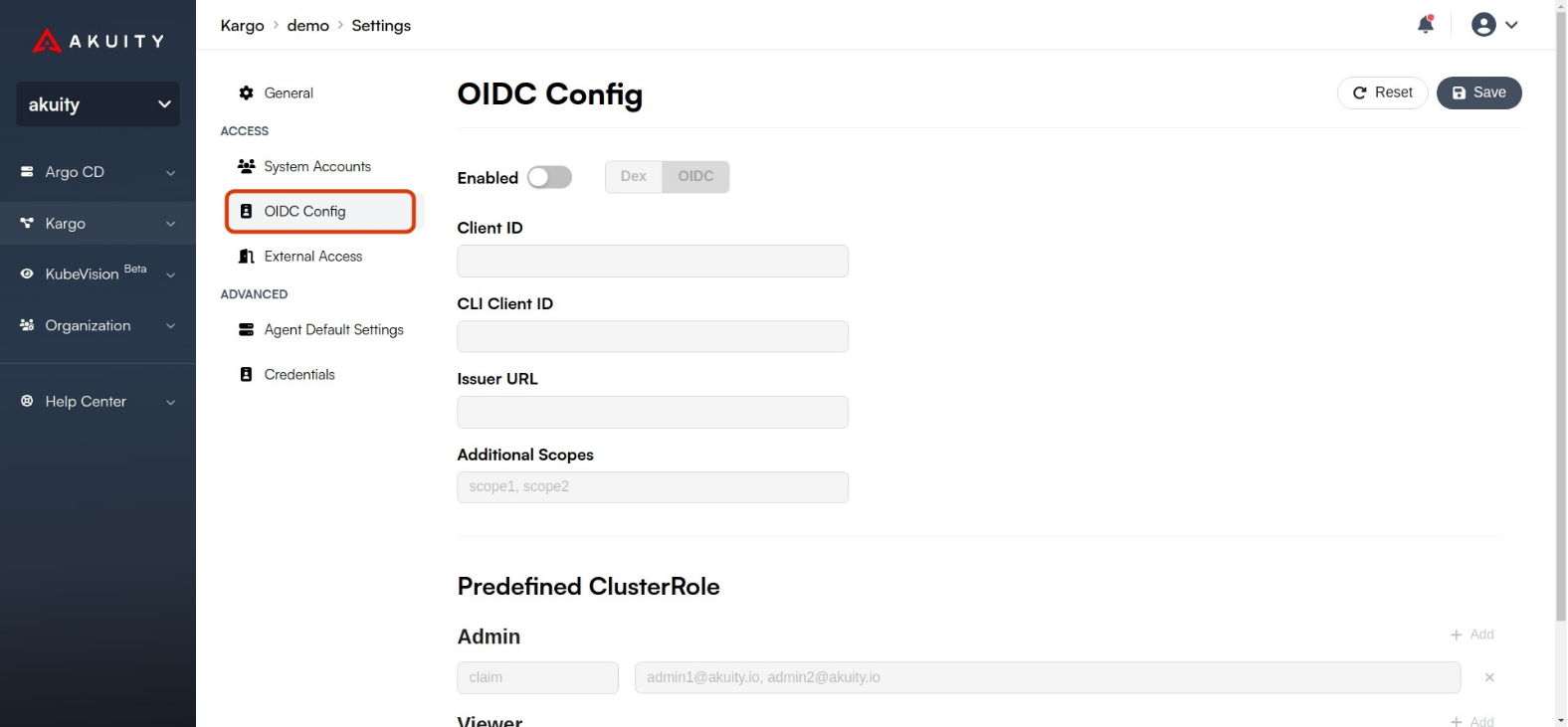
In the left panel, search for Access and go to OIDC Config.
-
Click on the Enabled toggle to enable OIDC and choose your desired
Type.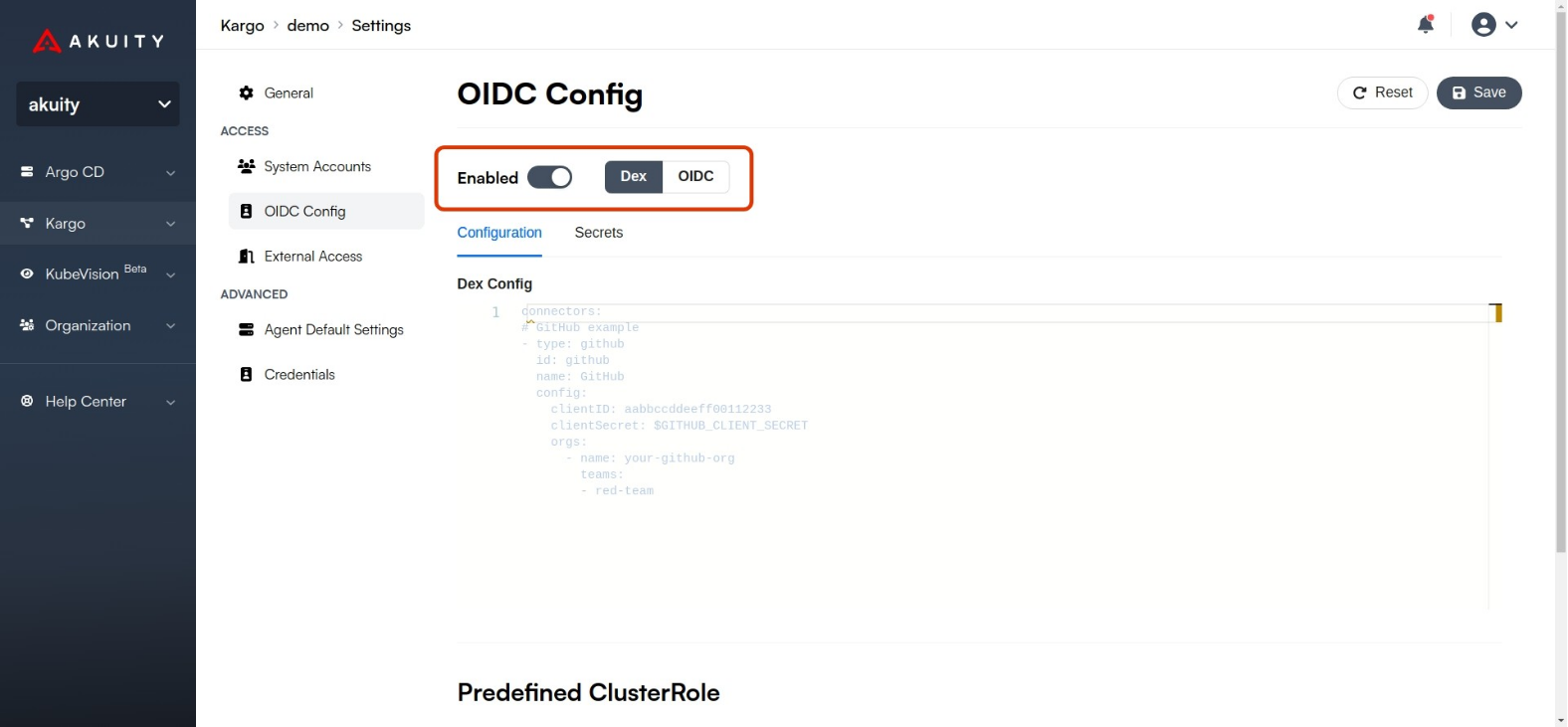
Okta
Working SAML Configuration with Okta
Below is an example Dex configuration for Okta:
connectors:
- type: saml
id: okta
name: OKTA
config:
ssoURL: https://yourorganization.oktapreview.com/app/yourorganizationsandbox_appname/sso/saml
redirectURI: https://<kargo_instance_id>.kargo.akuity.cloud/dex/callback
usernameAttr: name
emailAttr: email
groupsAttr: groups
caData: <certificate from IdP>
Reference: https://dexidp.io/docs/connectors/saml/
Steps to configure Okta for SSO with SAML:
-
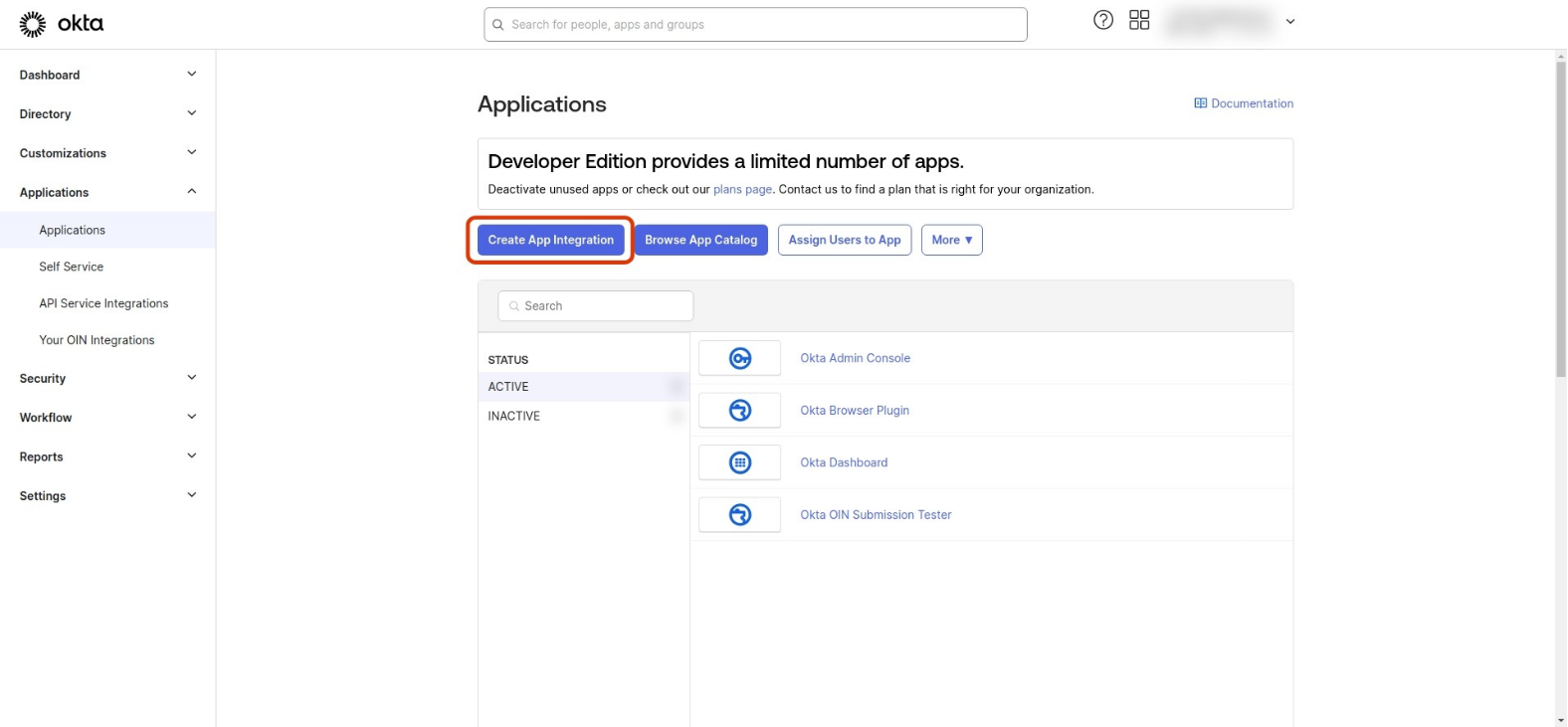
In your Okta Admin Dashboard, Go to Applications -> Applications -> Create App Integration
-
Select SAML 2.0 and click Next
-
Give your application a name and click Next
-
In Configure SAML section, enter the following details:
-
Single sign on URL:
https://<kargo_instance_id>.kargo.akuity.cloud/dex/callback -
Audience URI (SP Entity ID):
https://<kargo_instance_id>.kargo.akuity.cloud/dex/callback -
In the Attributes Statements section add :
Name Name format Value email Unspecified user.email name Unspecified user.fullName -
In the Group Attribute Statements section add the following, (you can modify the group regex according to your needs) :
Name Name format Filter groups Unspecified Matches regex : .* -
Click Next and Finish
-
-
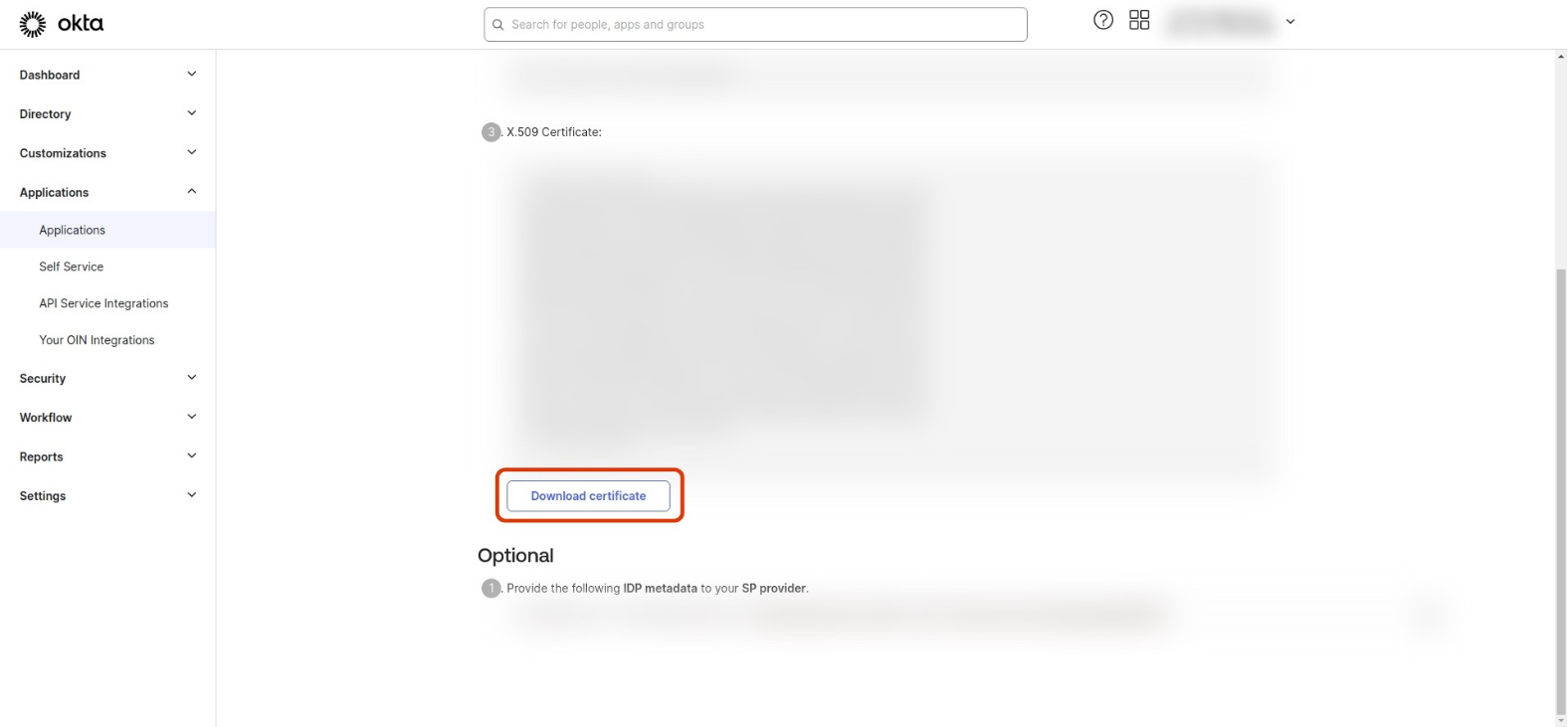
Go to the Application details page, select Sign On tab and then find and click the View SAML setup instructions button on the right side.
-
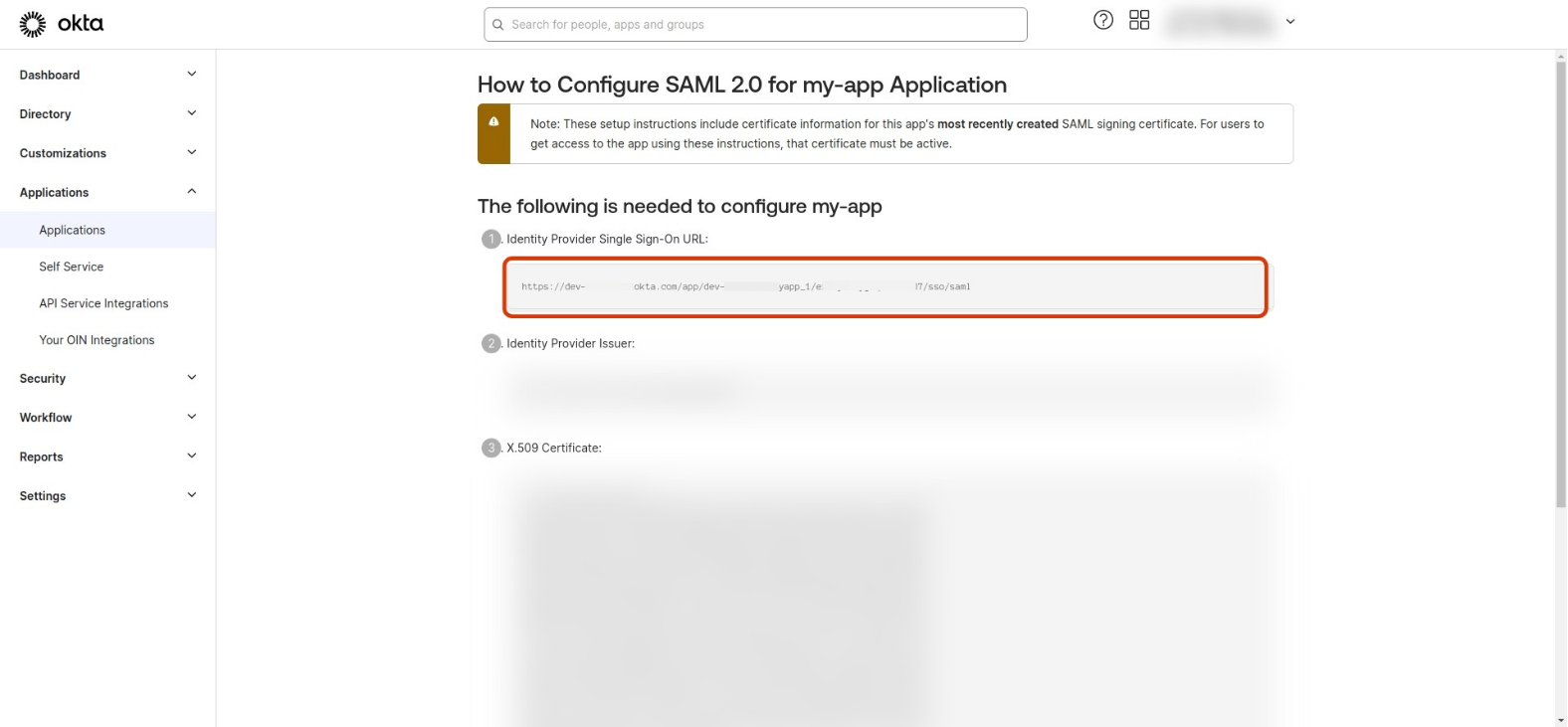
Copy the Identity Provider Single Sign-On URL and use it for ssoURL: in the Dex config.
-
Download the Certificate and base64 encode it, then apply it to your Dex config.