Akuity Platform SSO
The Akuity Platform supports the following Single Sign-On (SSO) providers:
- Microsoft (Azure AD)
- Google Workspace
- Okta
- OpenID Connect
- SAML
Akuity Platform SSO is available on Enterprise plans only. Please contact our Sales Team to access the feature.
Note that this feature only applies to the Akuity Platform, and is separate from SSO for Argo CD. Argo CD SSO is available in all Professional and Enterprise plans.
Configuring SSO
The owner role on the Organization is required to configure SSO.
To configure SSO for an Organization on the Akuity Platform:
-
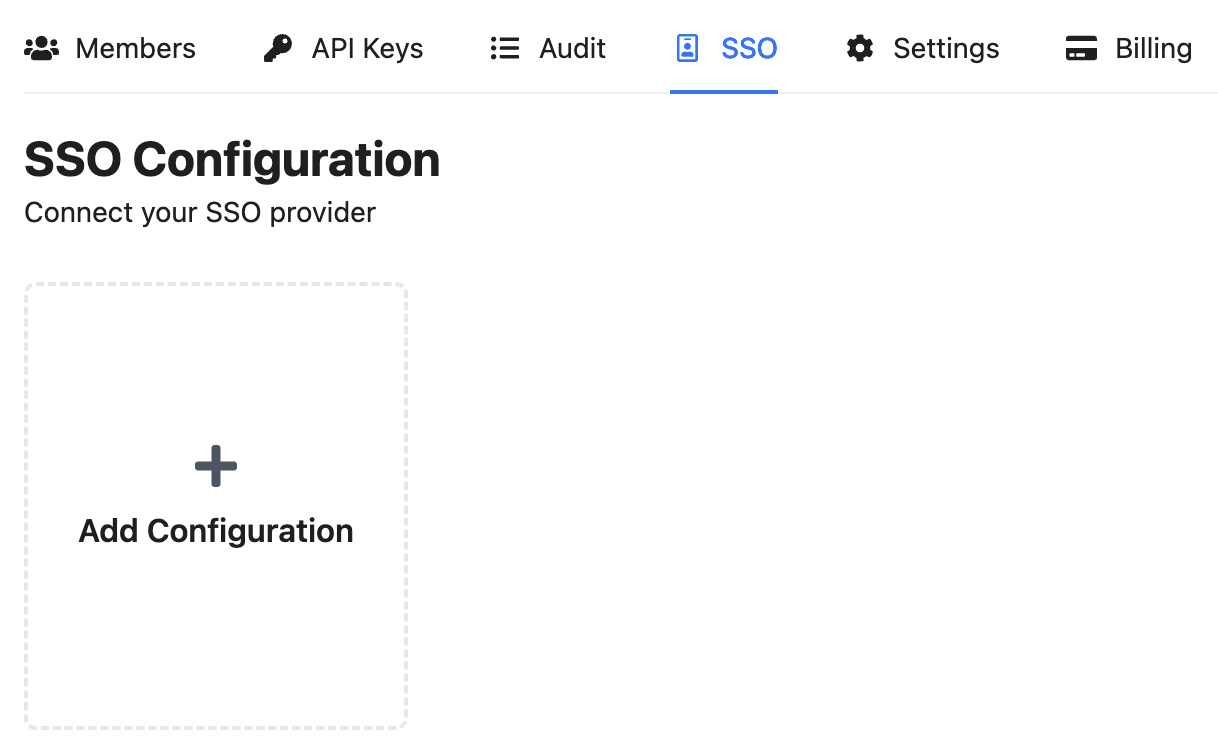
Go to Organization > SSO.
-
Click Add Configuration.
- Microsoft (Azure AD)
- Google Workspace
- Okta
- OpenID Connect
- SAML
- Okta with SAML
-
Register an application with the Microsoft identity platform with the following settings:
- Set Redirect URI to
https://auth.akuity.io/login/callback
- Set Redirect URI to
-
Add the following Delegated Permissions to the registered application:
Users > User.ReadDirectory > Directory.Read.All
-
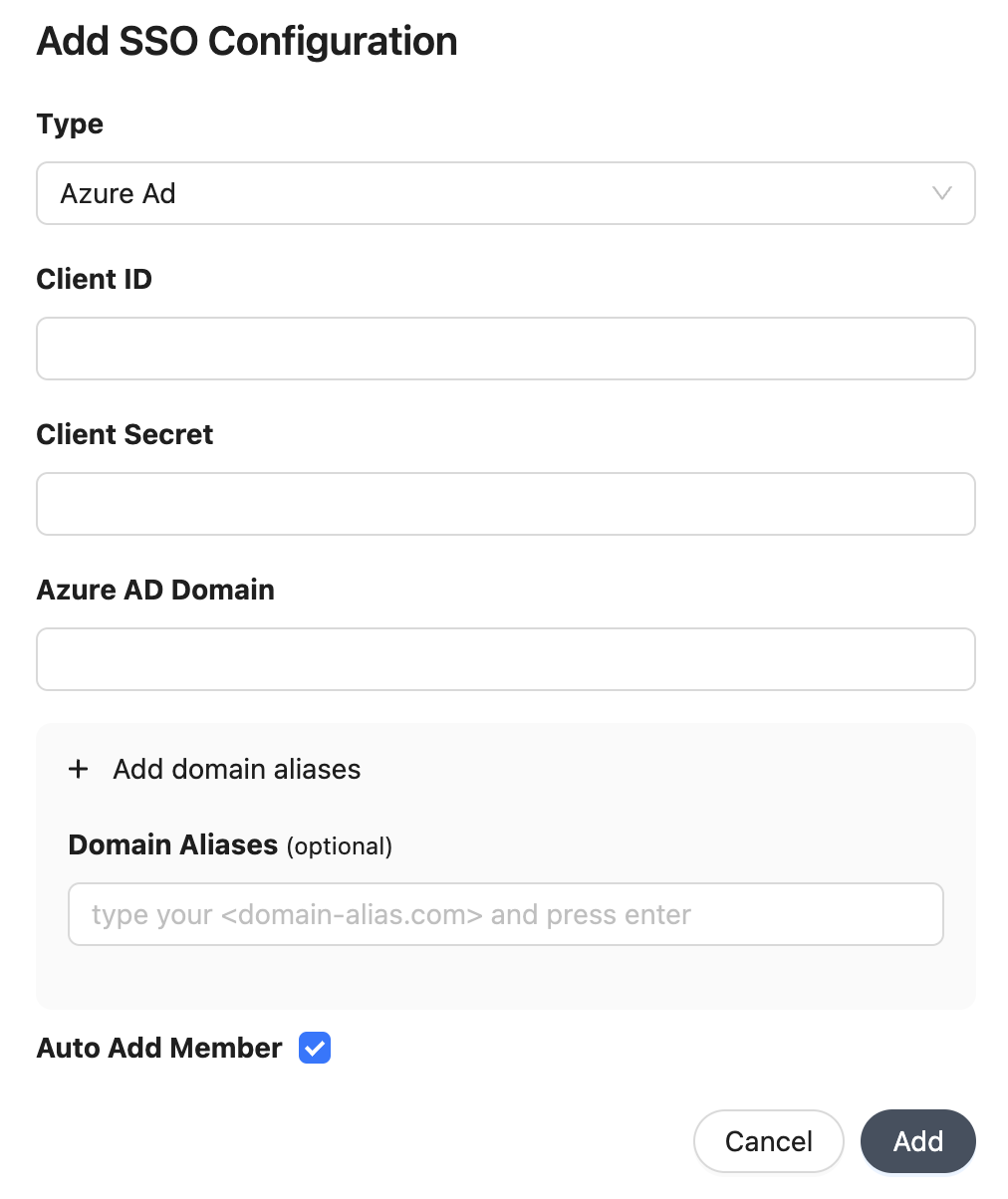
Populate the configuration details inside the form:
- Client ID: Application (client) ID
- Client Secret: Client Secret
- Azure AD Domain: Your Azure AD domain name. You can find this on your Azure AD directory's overview page in the Microsoft Azure portal.
- Domain Aliases: Additional domains to match organization members (e.g.
some-org.com). - Auto Add Member: Allow your organization members to join your organization with the
memberrole automatically.
For security purposes, your domain and domain aliases will be submitted to Akuity for manual review and approval.
-
Register an application to the Google Workspace with the following settings:
- Authorized JavaScript origins to
https://auth.akuity.io - Set Redirect URI to
https://auth.akuity.io/login/callback
- Authorized JavaScript origins to
-
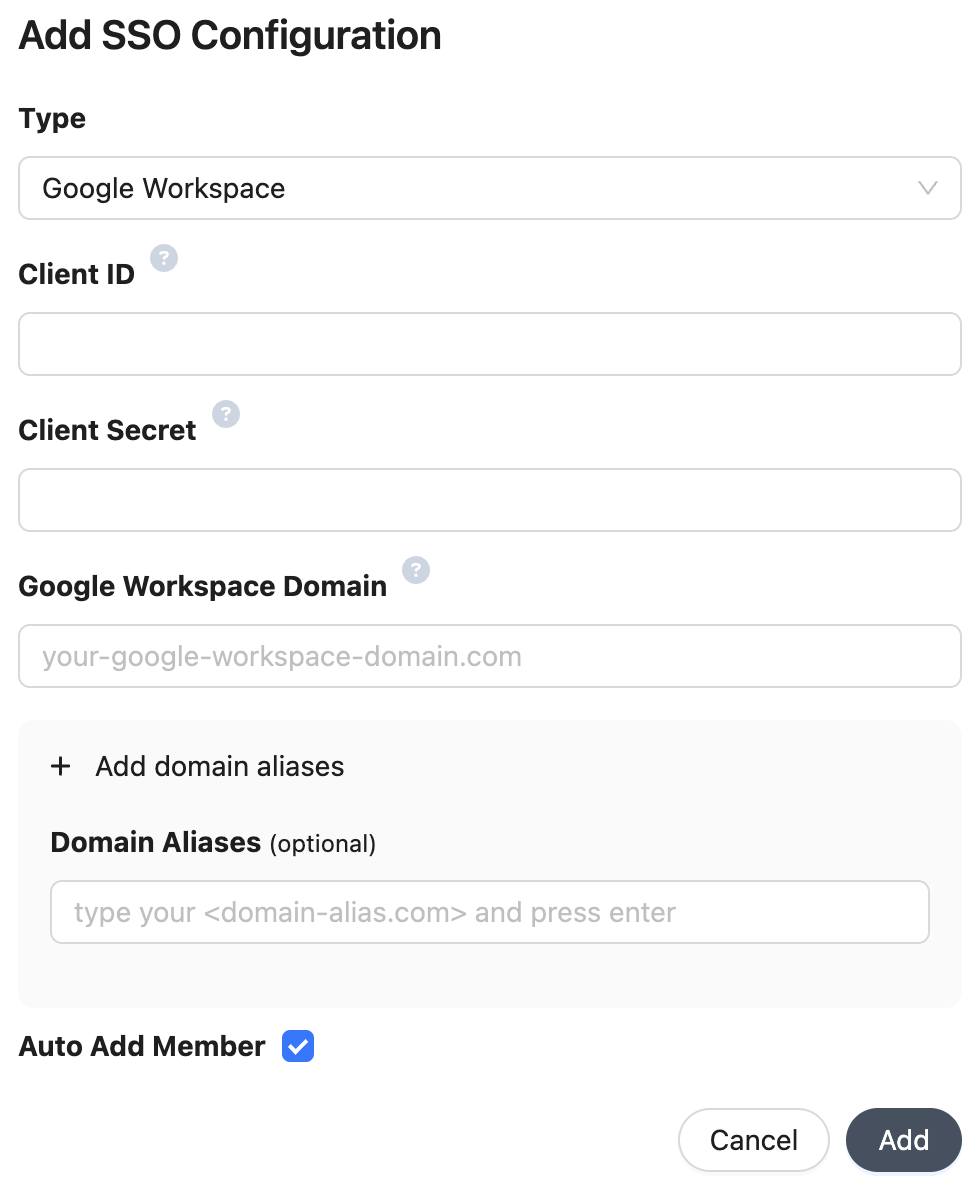
Populate the configuration details inside the form:
- Client ID: Application (client) ID
- Client Secret: Client Secret
- Google Workspace Domain: Google Workspace domain name for your organization.
- Domain Aliases: Additional domains to match organization members (e.g.
some-org.com). - Auto Add Member: Allow your organization members to join your organization with the
memberrole automatically.
For security purposes, your domain and domain aliases will be submitted to Akuity for manual review and approval.
- Test the connection.
Okta native integration does not support groups claim, please use generic SAML/OIDC instead if you want to use IDP groups mapping features.
-
Create an Okta OIDC Application.
- In your Okta Admin Dashboard, Select Applications > Applications, and Create App Integration.
- Select Create New App.
- Choose OIDC as the Sign-in method and Web Application as Application Type.
- Set Sign-in redirect URIs with
https://auth.akuity.io/login/callbackand select Create. - Copy your
Client IDandClient Secret. - (Optional) You can configure
Initiate login URI to skip Akuity login page.- Set
Login initiated by underGeneral Settings asEither Okta or App - Set
Login flow asOIDC Compliant - Set
Initiate login URI ashttps://akuity.cloud/api/auth/login/sso/<your-organization-id>Organization tab in Akuity Dashboard)
- Set
-
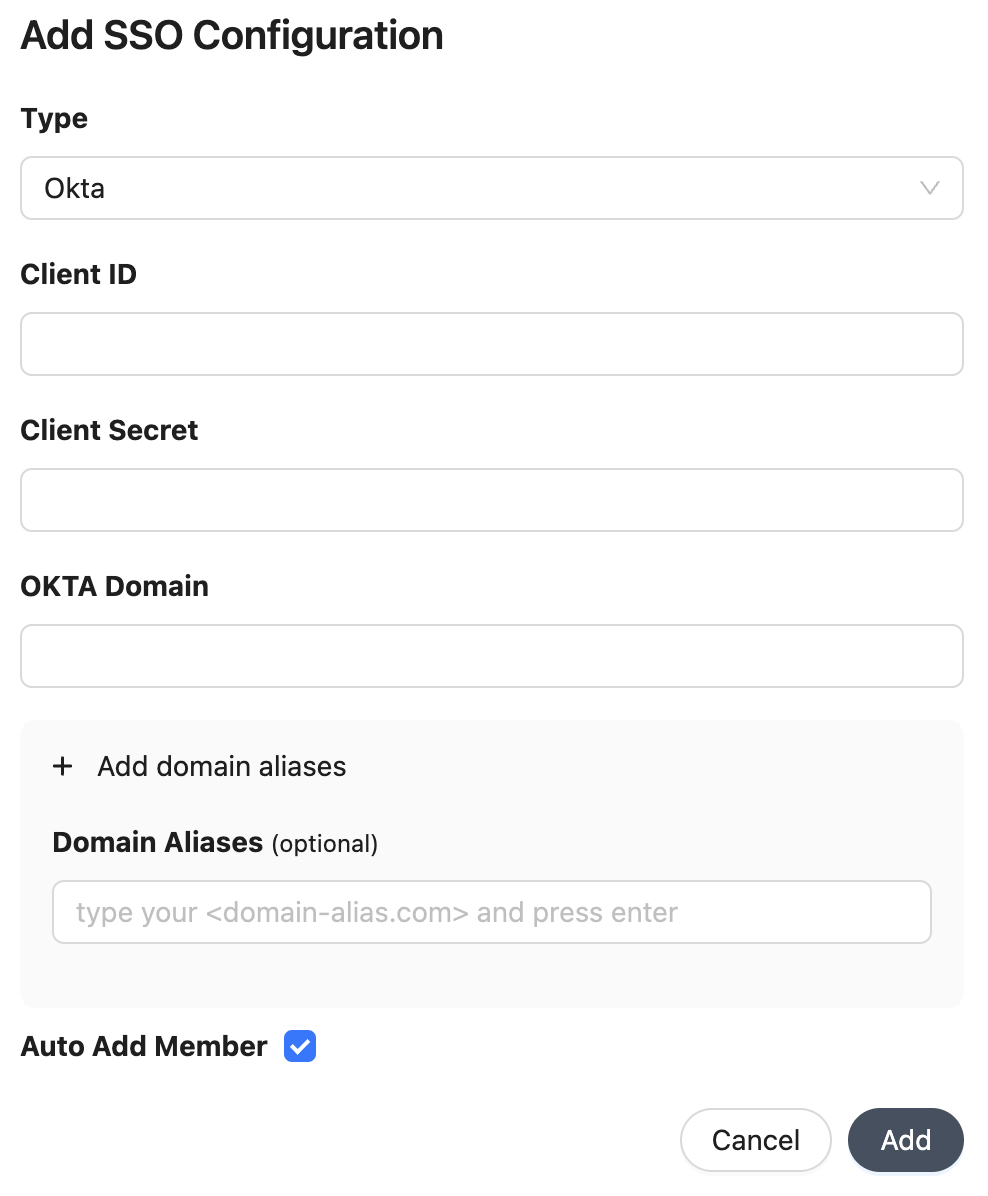
Populate the configuration details on the form.
- Client ID: Okta OIDC Application Client ID
- Client Secret: Okta OIDC Application Client Secret
- Okta Domain: Your Okta domain.
- Domain Aliases: Additional domains to match organization members (e.g.
some-org.com). - Auto Add Member: Allow your organization members to join your organization with the
memberrole automatically.
For security purposes, your domain and domain aliases will be submitted to Akuity for manual review and approval.
-
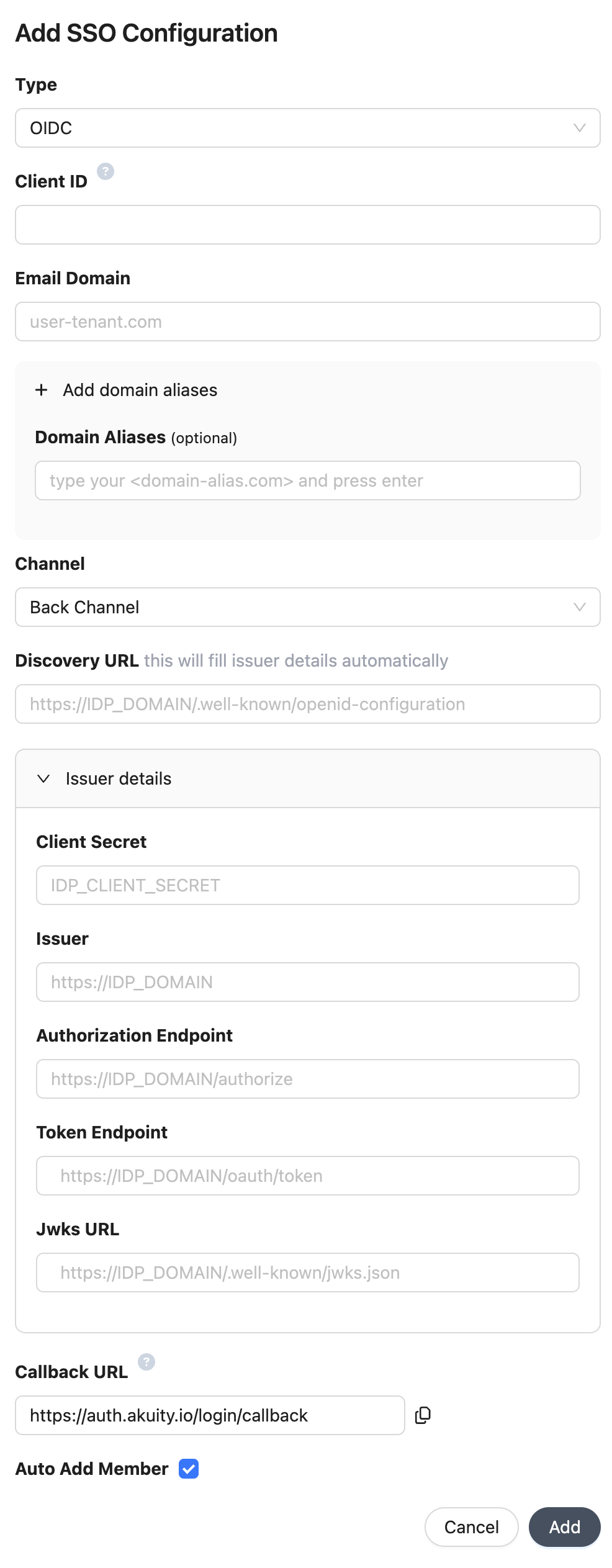
Create an OIDC Application.
- Set Allowed Callback URL to
https://auth.akuity.io/login/callback
- Set Allowed Callback URL to
-
Populate the configuration details on the form.
- Client ID: OIDC Application Client ID
- Email Domain: Your organization's domain name
- Domain Aliases: Additional domains to match organization members (e.g.
some-org.com). - Channel:
Front Channelusesresponse_mode=form_postandresponse_type=id_tokenBack Channelusesresponse_type=code
- Discovery URL: OIDC Discovery URL to fill Issuer details
- Issued details:
- Client Secret: OIDC Application Client Secret (required for the
Back Channel) - Issuer: URL of the Issuer Identifier.
- Authorization Endpoint: URL of the OpenID Provider's OAuth 2.0 Authorization Endpoint.
- Token endpoint: URL of the OpenID Provider's OAuth 2.0 Token Endpoint (required for the
Back Channel). - Jwks URL: URL of the OpenID Provider's JSON Web Key Set document.
- Client Secret: OIDC Application Client Secret (required for the
- Auto Add Member: Allow your organization members to join your organization with the
memberrole automatically.
For security purposes, your domain and domain aliases will be submitted to Akuity for manual review and approval.
-
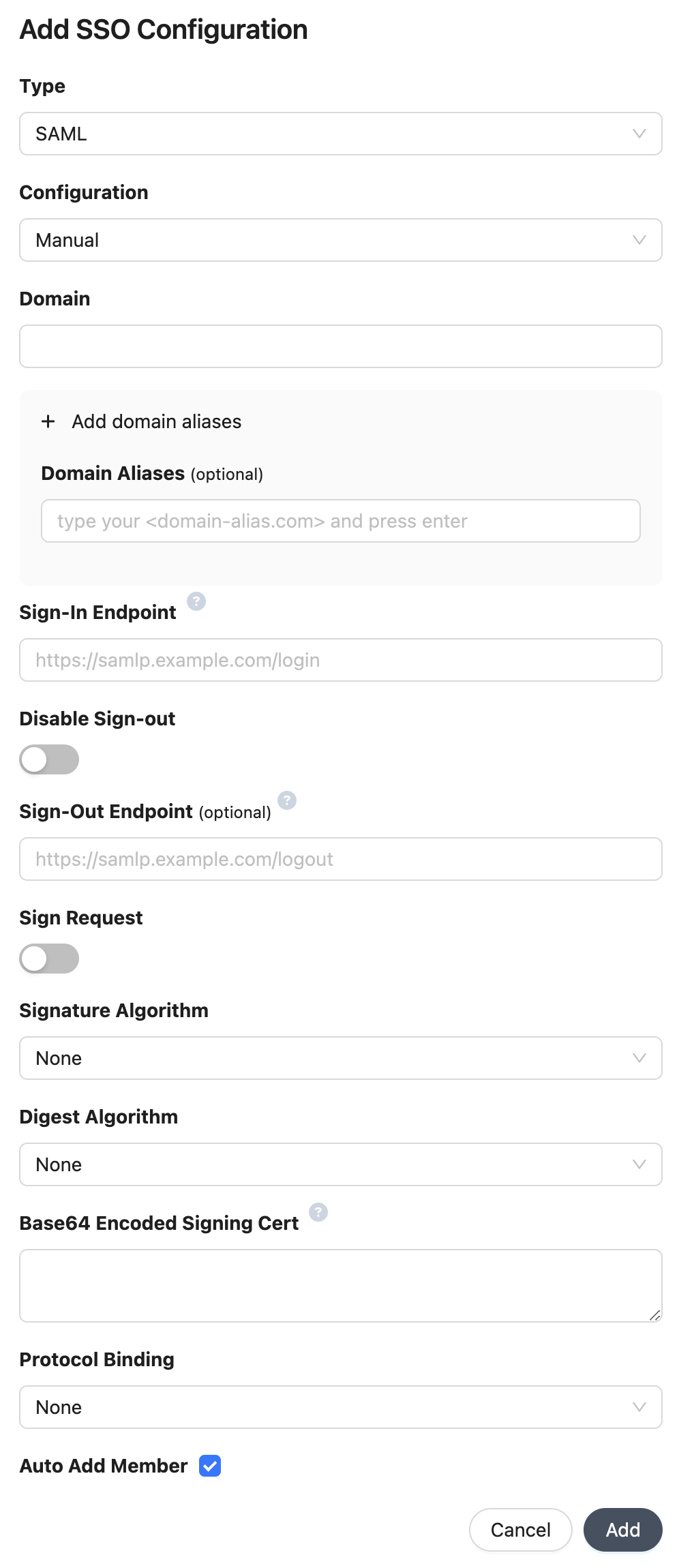
Create an OIDC Application.
-
Set Allowed Callback URL to
https://auth.akuity.io/login/callback?connection={your organization id} -
Set Entity ID to
urn:auth0:akuity:{your organization id} -
Organization ID can be found in the top-right side of the
Organizationpage.
-
-
Populate the configuration details on the form.
- Domain: Your organization's domain name
- Domain Aliases: Additional domains to match organization members (e.g.
some-org.com). - Configuration (XML): Use Metadata XML to configure SAML SSO.
- Configuration (Manual): Manually configure SAML SSO.
- Sign-In Endpoint: SAML single login URL.
- Disable Sign-out: When disabled, a specific Sign Out URL can be set.
- Sign-Out Endpoint: SAML single logout URL.
- Sign Request: When enabled, the SAML authentication request will be signed.
- Signature Algorithm: Algorithm to use to sign the SAML assertions.
- Digest Algorithm: Algorithm to use to the sign request digest
- Base64 Encoded Signing Cert: Base64 encoded signing certificate
- Protocol Binding: HTTP binding supported by the IdP
For security purposes, your domain and domain aliases will be submitted to Akuity for manual review and approval.
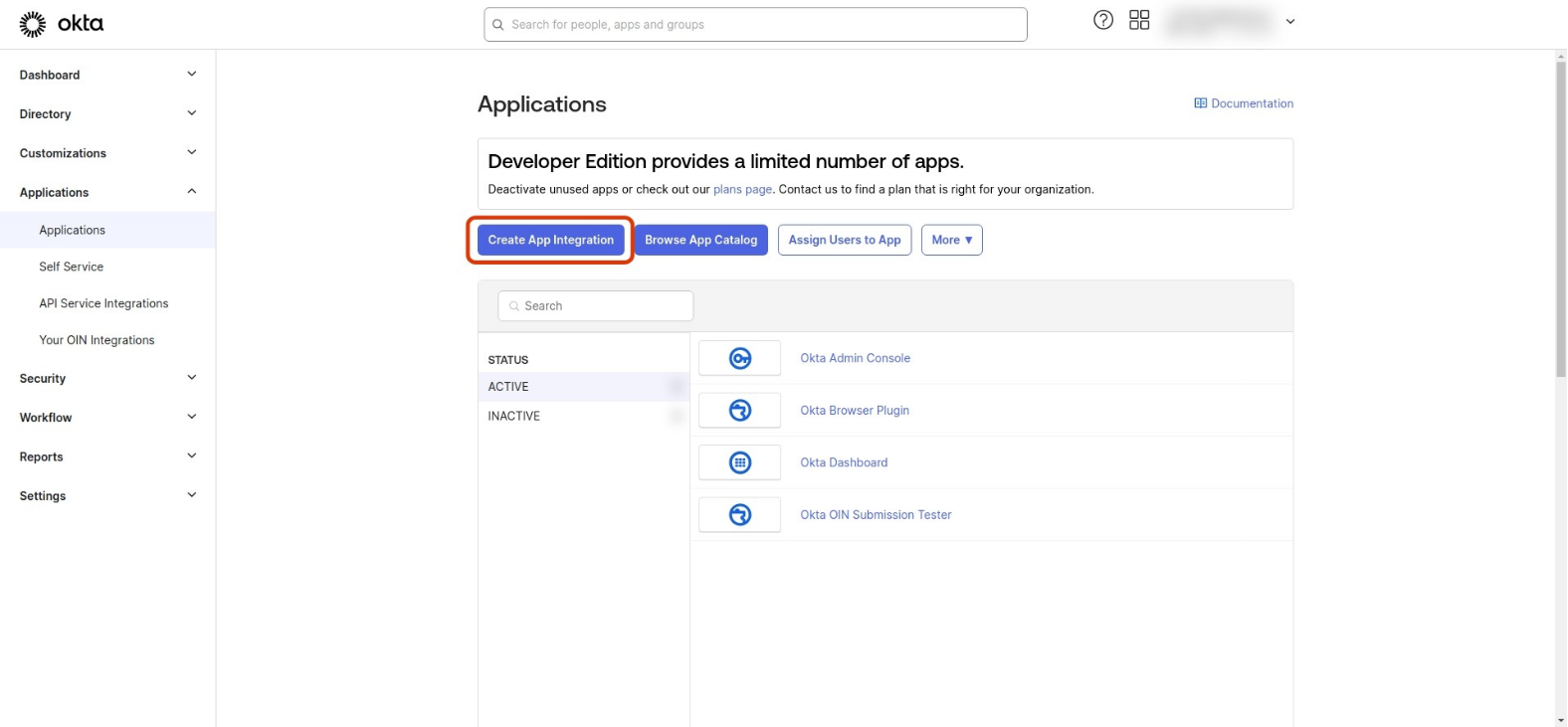
-
In your Okta Admin Dashboard, go to Applications -> Applications -> Create App Integration
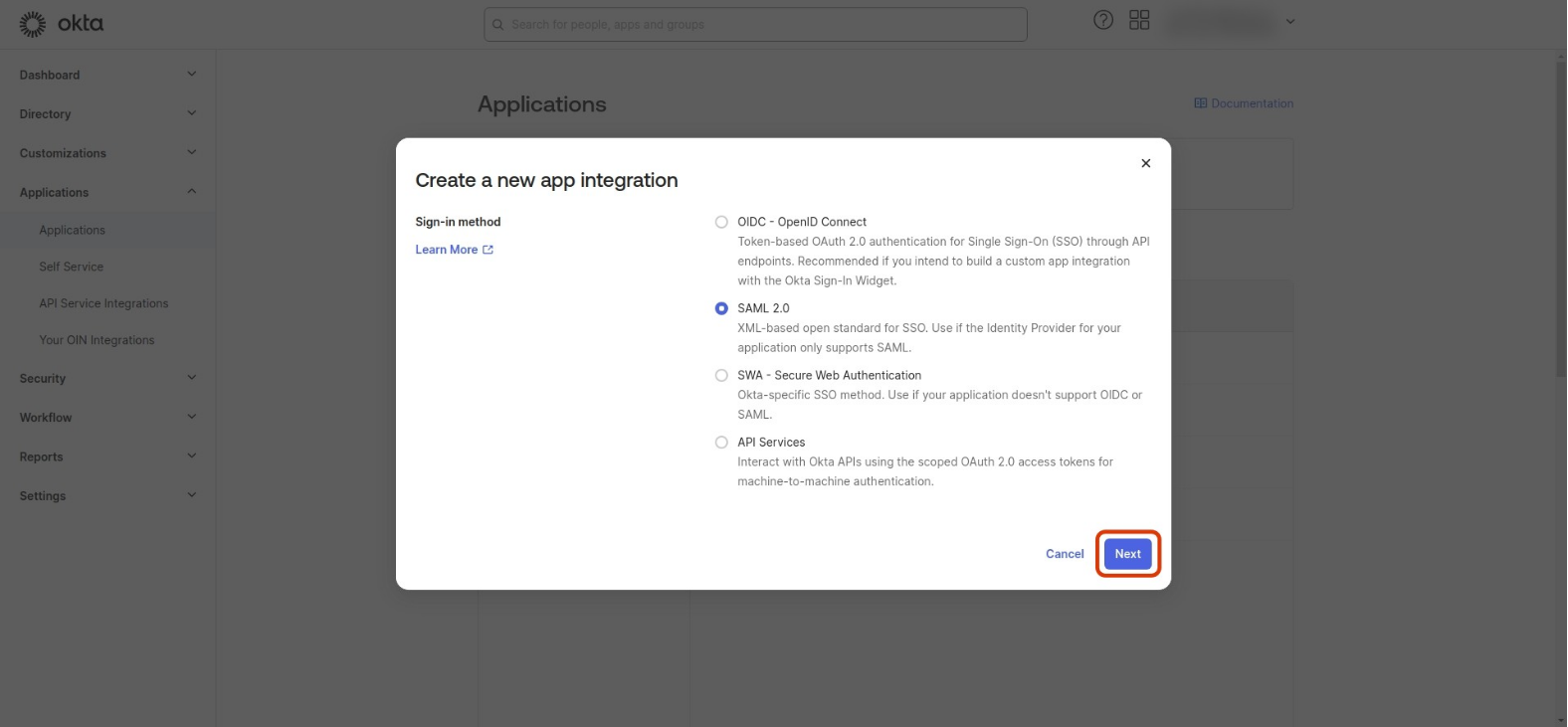
-
Select SAML 2.0 as the Sign-in method, and click Next
-
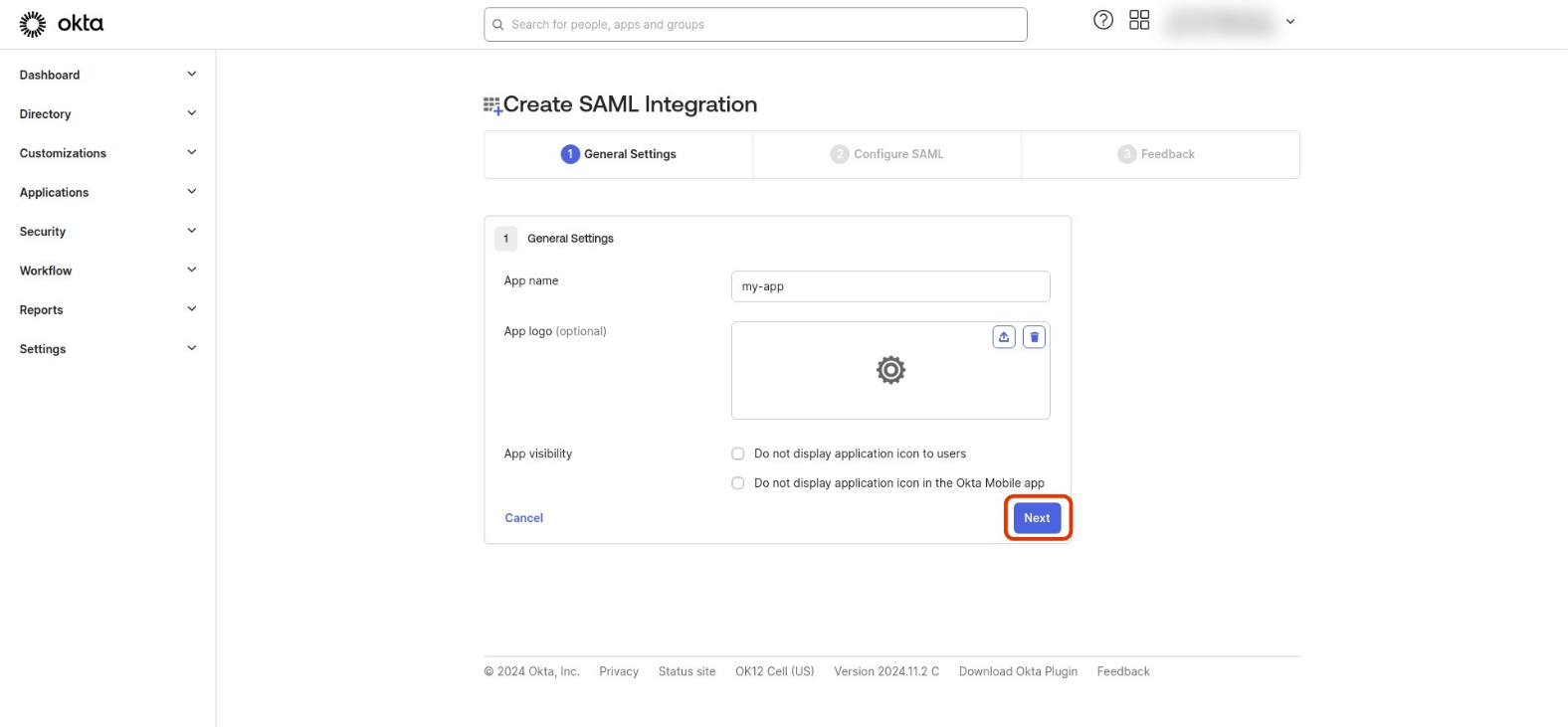
Provide the app name and logo, then click Next.
-
In Configure SAML section set :
a. Single Sign-On URL:
https://auth.akuity.io/login/callback?connection=<your_organization_id>b. Audience URI (SP Entity ID):
urn:auth0:akuity:<your_organization_id>c. In the Attributes Statements section, add :
Name Name format Value email Unspecified user.email given_name Unspecified user.firstName family_name Unspecified user.lastName d. In the Group Attribute Statements section, add the following (you can modify the group regex according to your needs) :
Name Name format Filter groups Unspecified Matches regex : .*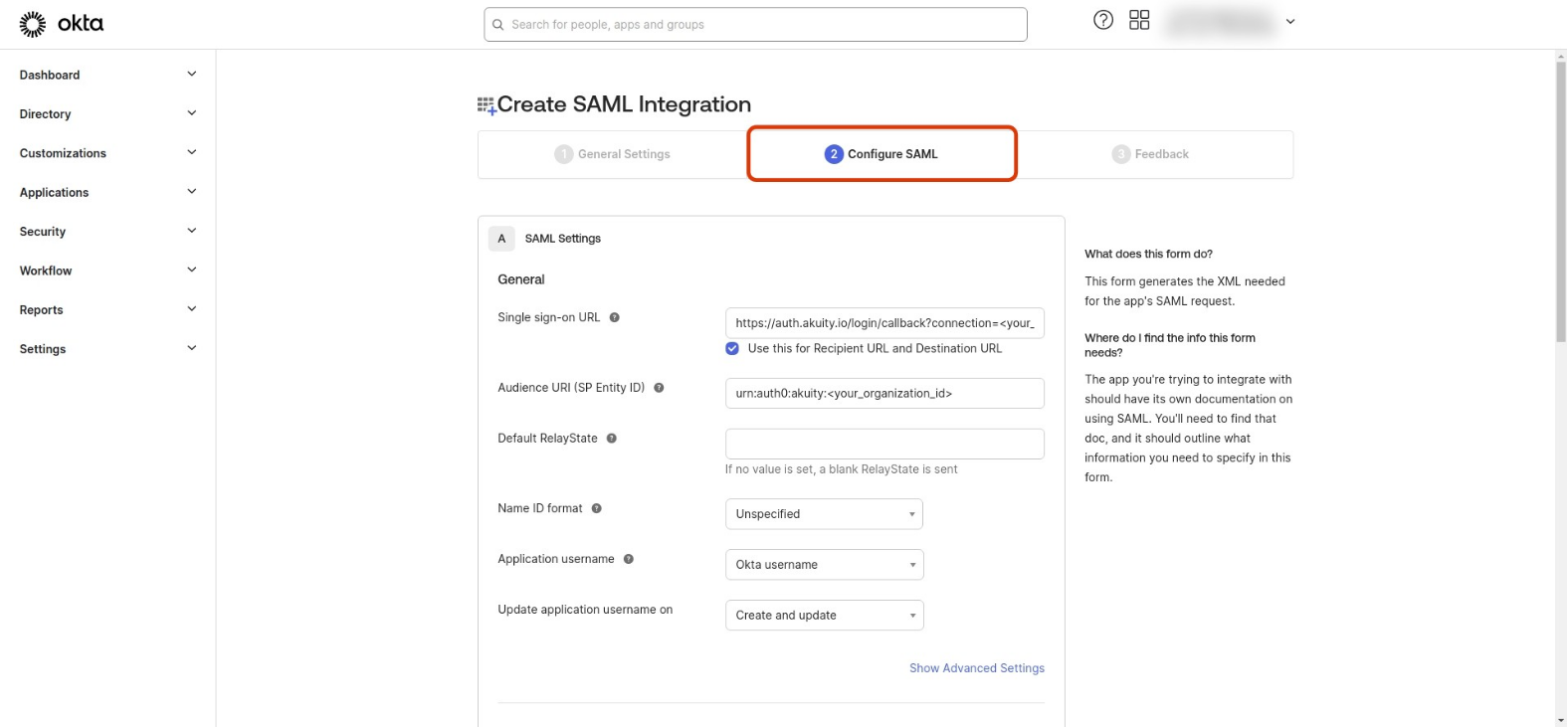
e. Click Next and Finish
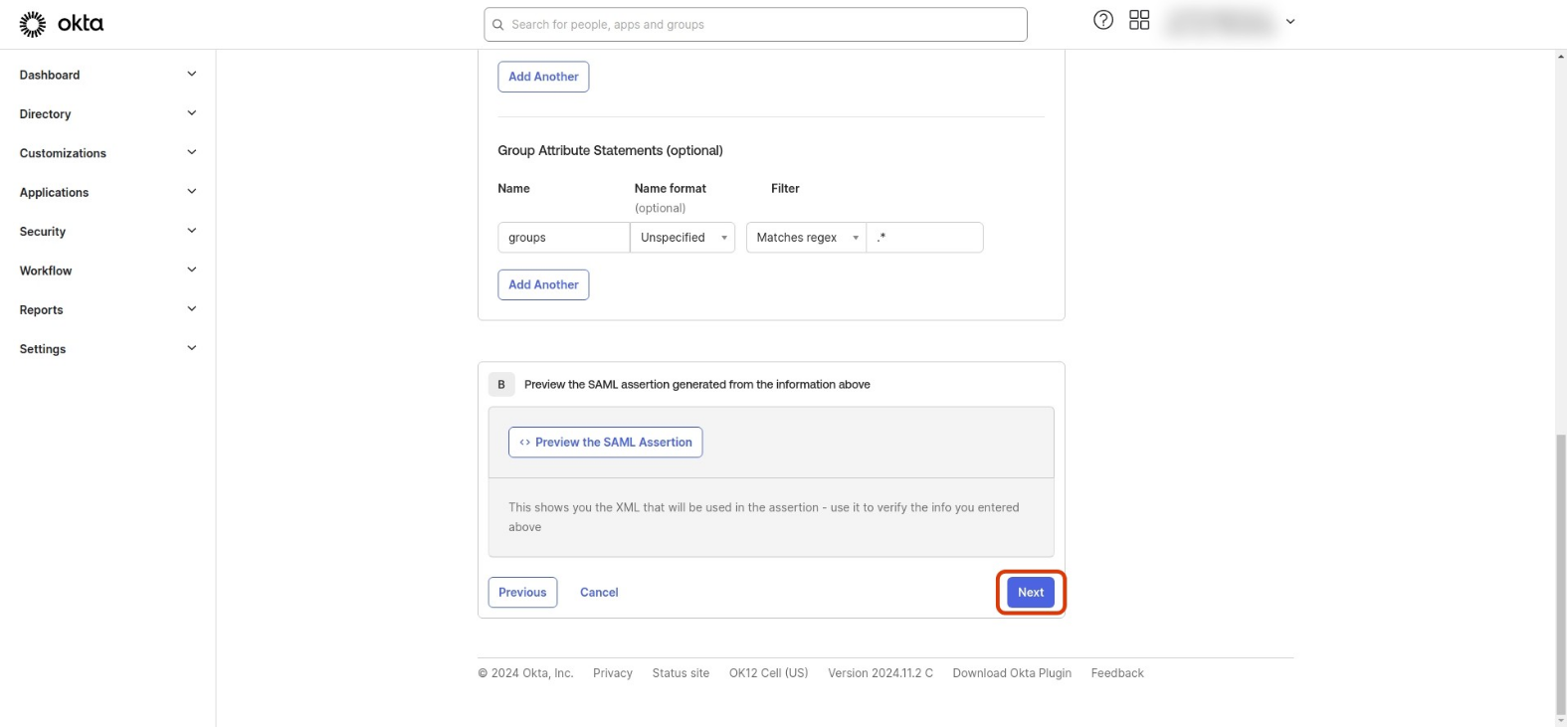
-
Go to the Application details page, select Sign On tab and then find and click the View SAML setup instructions button on the right side
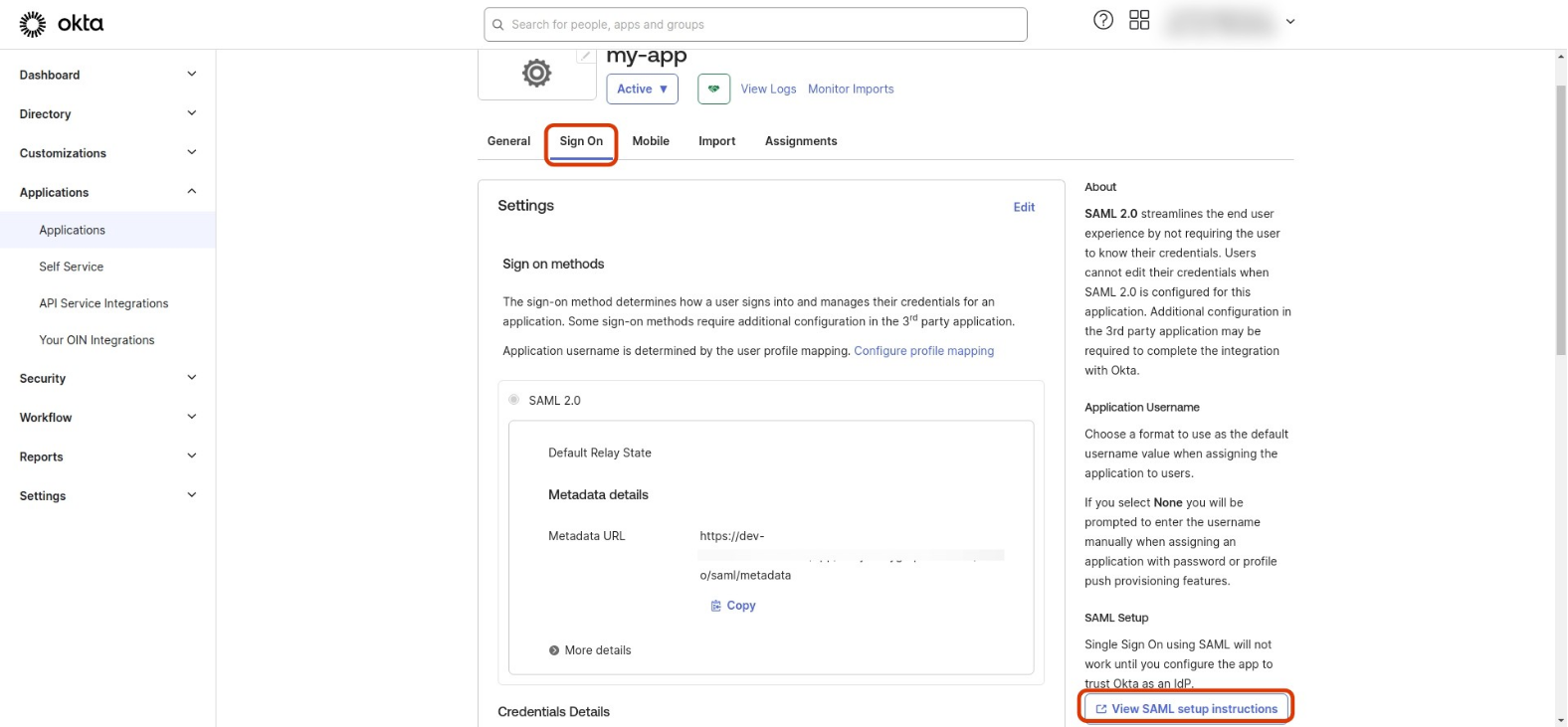
-
This will open a
How to Configure SAML 2.0 for <app-name> Applicationpage, where you can find the XML IDP metadata. Copy the XML.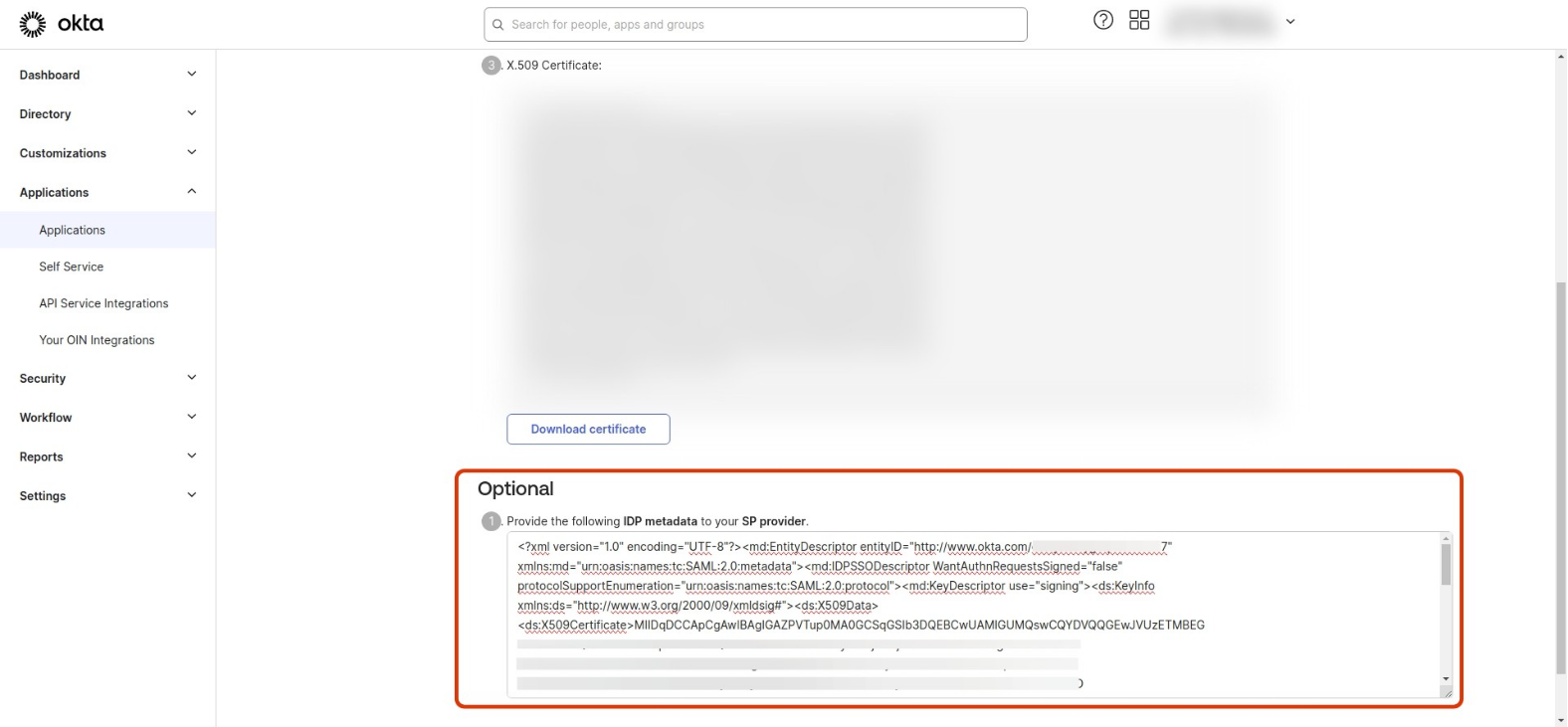
-
Now, go to Akuity, and from the Type dropdown select SAML.
-
Choose XML as the Configuration type and paste the Metadata you copied in the Metadata XML input.
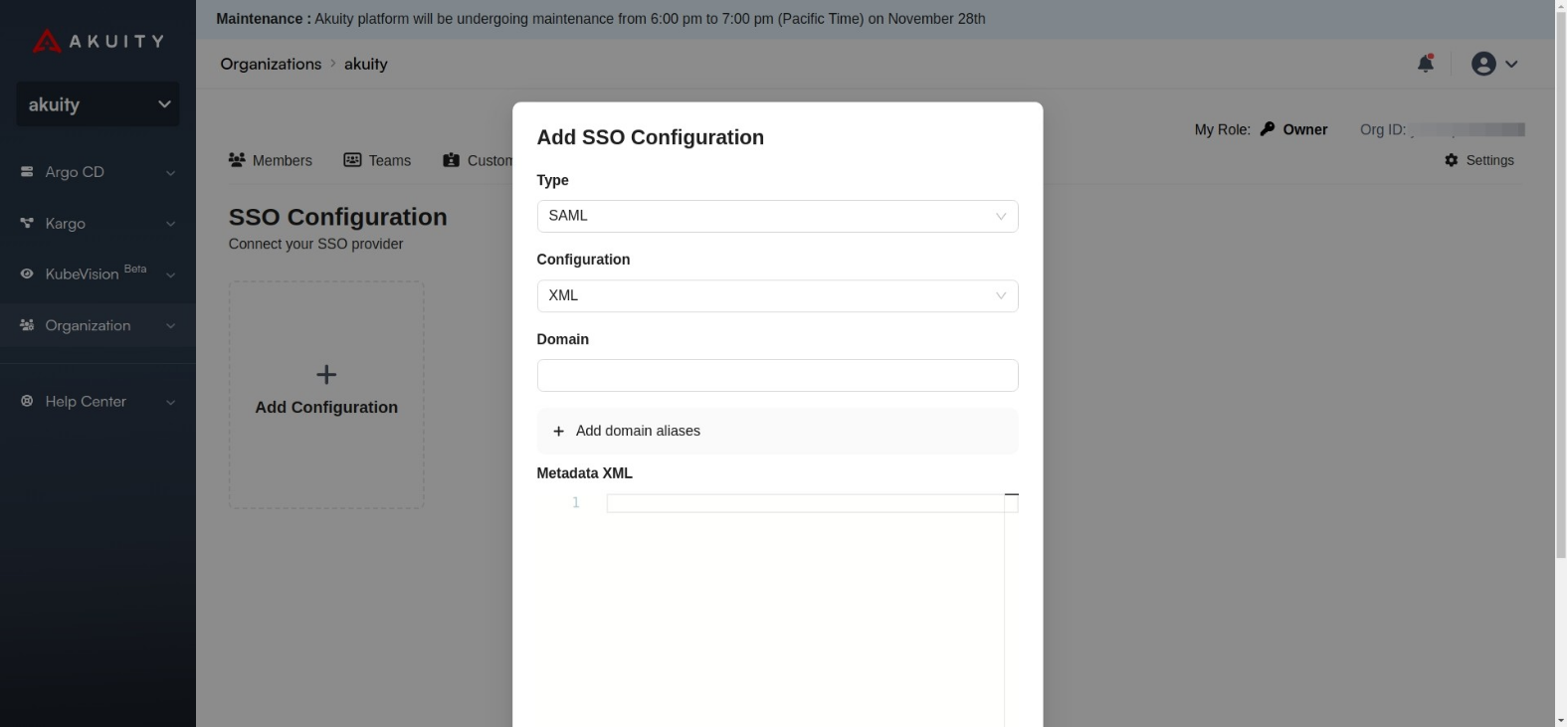
-
Add your SSO email domain in the Domain input field and create the configuration by clicking the Add button.
-
Now, if you try to log in with an email associated with the domain you just configured, you will be redirected to Okta.
IDP Groups Mapping
IDP Groups does not work for Okta native integration as Okta does not support groups claim. Please use generic SAML/OIDC option instead to connect with Okta if you want to use this feature.
To configure IDP Groups for an Organization in the Akuity Platform:
-
Go to Organization > SSO.
-
Click Add New Rule.
-
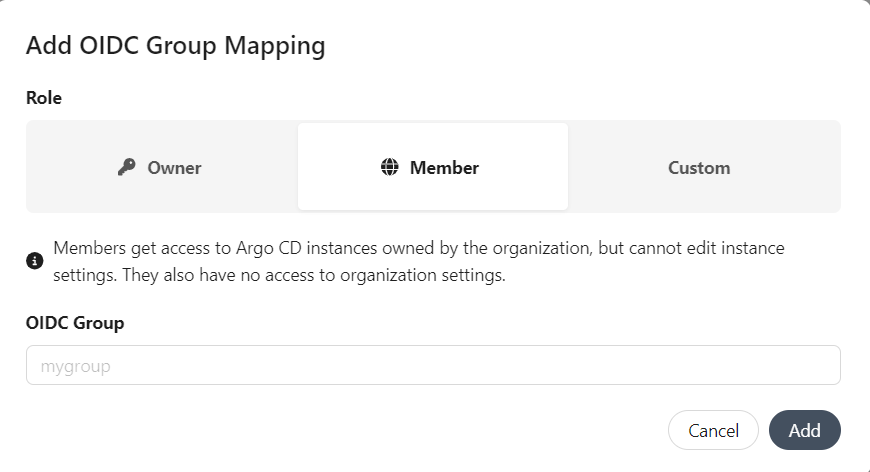
In the Add OIDC Group Mapping select the role and specify the corresponding OIDC Group for your provider.
-
Click the Add button.
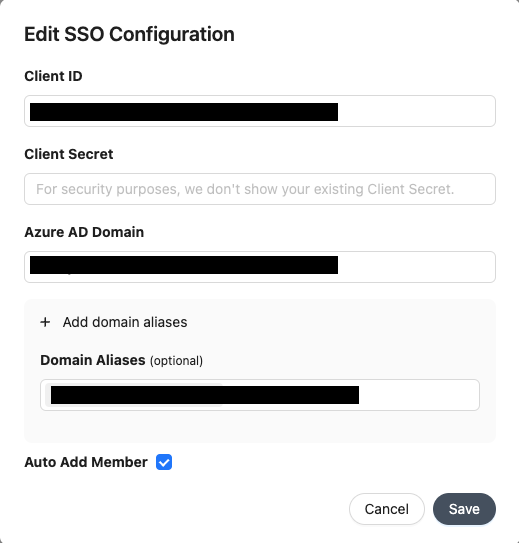
In the SSO settings, if the Auto Add Member is checked the new user willjoin your organization with the member role automatically.
OIDC Team Mapping
OIDC Team Mapping does not work for Okta native integration as Okta does not support groups claim. Please use generic SAML/OIDC option instead to connect with Okta if you want to use this feature.
This feature allows you to map users with a specific OIDC group to a team in your organization.
Your organization must have at least one Team.
To configure this feature for an Organization in the Akuity Platform:
-
Go to Organization > SSO.

-
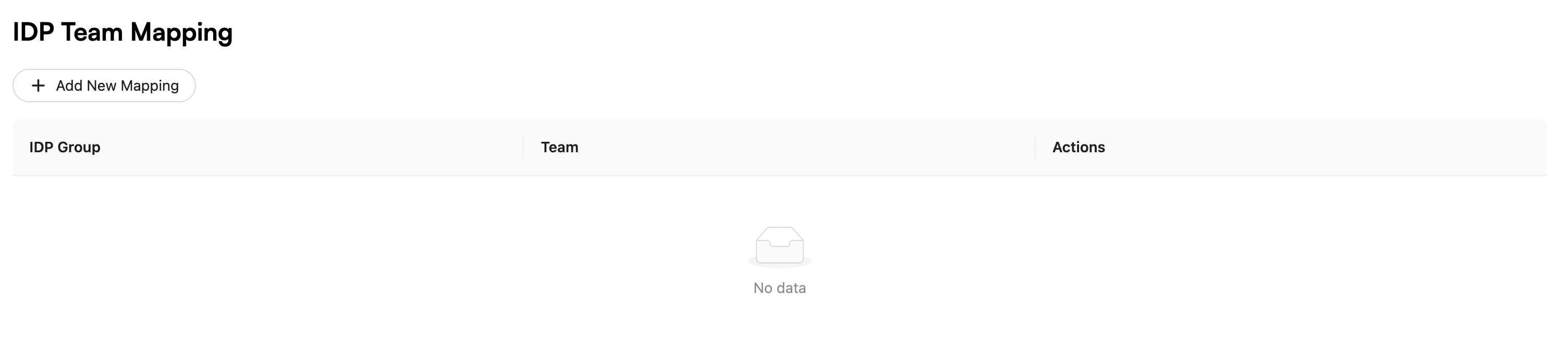
Scroll down to the "OIDC Team Mapping" section and click Add New Mapping.
-
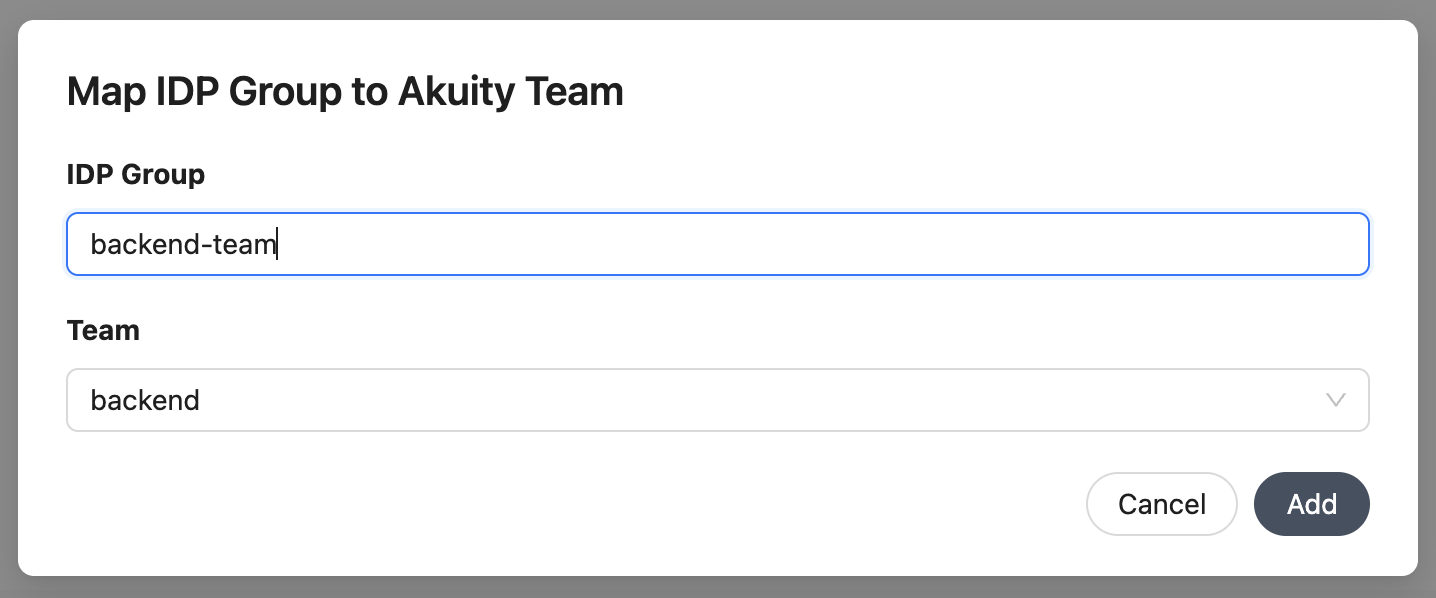
In the modal that appears, specify an OIDC group and select an existing team from the dropdown.
-
Click the Add button.
Now, when a user logs in with the specified IDP group, they will be added to the selected team in your organization.